What we do
Malware Removal
The Internet ecosystem today advancing at a pace like never before, and along with its advancement, so are the threats to the ecosystem. We all have been through the dreaded process of removing viruses from our computers..
Website Backup
Be rest assured, with our website backup processes, you never to have to lose a minute of peace. With structured processes in place, a copy of your website is created every night, to ensure that you don't lose any..
Web Application Security?
Web application security also known as cyber security refers to the process that secures your websites, web services and web applications from exploitation by the hackers. Poor coding, bad design techniques, and mistakes..
Mobile Application Security
With the advancement of data technology the risks of vulnerability are increasing day by day which leads to the loss of personal information and data, and the hacked data/information is than misused by hackers for illegal..
Source Code Review
It is a technique to identify security loopholes that may enable a hacker to exploit the application, system, and network security. This is achieved through a combination of human effort and technology support and..
Penetration Testing Service
In the digital world, cyber frauds and cyber crimes are increasing day by day. Therefore it is necessary to secure your systems from threats posed by the cyber-attacks or hackers. To make your task simpler, we..
Service Asset and Configuration Management
It is one of the first ITIL processes implemented in any organization. SACM is all about planning and managing..
System Integration Services
The system integration process refers to a complex building process that allows the coordination of different computing systems and software applications, functionally..
Application Hardening
As cyber crimes are increasing day by day it is very important for you to secure your IT infrastructure. Attackers can compromise an application’s integrity, bypass license, and authentication checks, and..
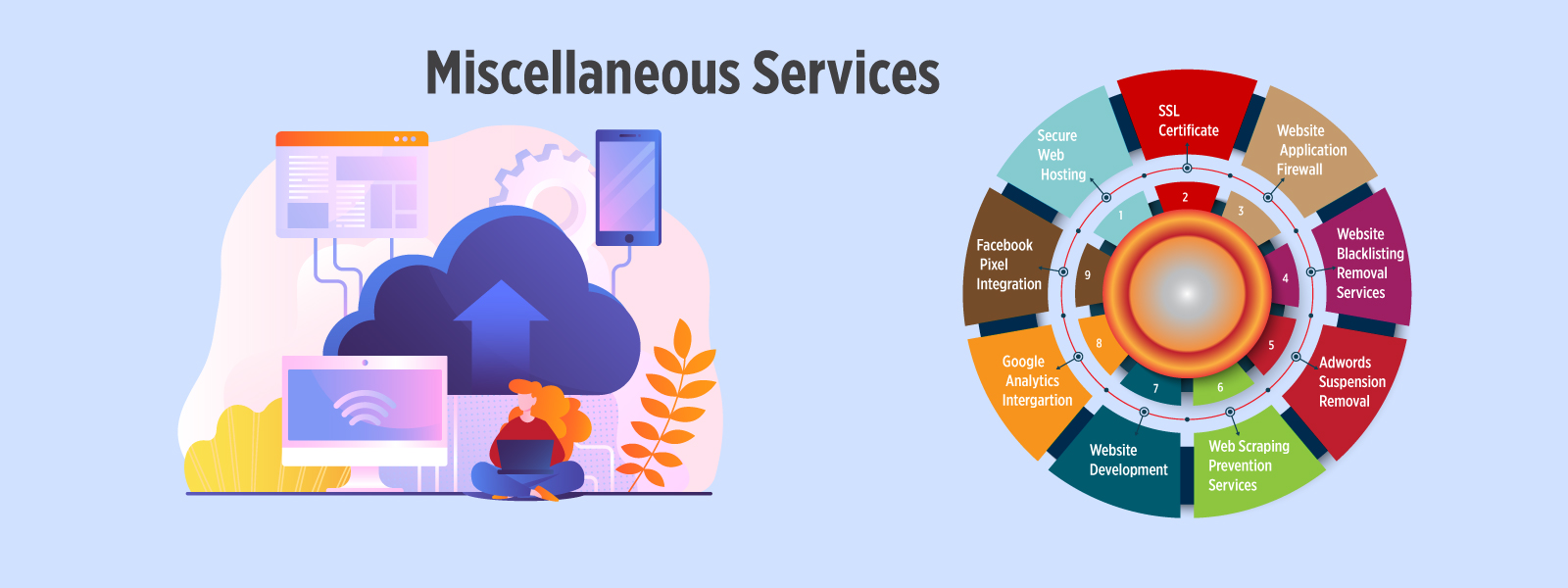
Secure Web Hosting
At CI Dragon, we deliver what we promise and will never trap you to give you awful experience or change our agreement later on. When you trust us then it is our responsibility to provide you with a..
SSL Certificate
SSL stands for Secure Sockets Layer that provides privacy, critical security and data integrity for both your website and your users’ personal information. Generally, SSL is used to secure credit..
Website Application Firewall
It may be integrated into the application code itself. This firewall is less expensive than the network-based firewalls. Host-based firewalls are difficult to manage as they require application..
Website Blacklisting Removal Services
A website is blacklisted when it is found to be involved in spammy activities, or is infected by malware, or is suspicious of malicious activities or when you download..
Adwords Suspension
A well-managed website helps you quickly position yourself on the search engine. Maintaining AdWords is a continuous process that requires constant attention in areas such as Keywords Research..
Web Scraping Prevention Services
It's essential to prevent your content from getting scraped by your competitors, as it is important to keep control of your well-deserved SEO traffic, or prevent misuse or abuse of your proprietary..
Website Development
Web development or website development is the process that is associated with the development of websites for the internet or the intranet. There are some technologies such as HTML, CSS, and JavaScript..
Facebook Pixel Integration
This tool offers enhanced conversion tracking that helps advertisers to obtain more data and information about their users and the performance of their Facebook Ads..
Security Risk and Gap Assessment
It assesses asset criticality regarding business operations and measure the risk ranking for assets and prioritize them for assessment..
Our Offerings
Our Story
CI Dragon was born out of the most prevalent need in the market, which is website security and managing governmental and cyber law compliances and procedures. Though most developers come with extensive experience in their respective fields, what most lack is the understanding and need to secure a website. With the ever-increasing pace of technological development and the direction the security industry is taking, our clients reached out to us for the security and compliance related solutions. With each client getting added to our array of growth partners, we finally structured and incorporated CI Dragon.


Latest Blog
Webcam Hacking – How to prevent webcam from hacking into your privacy?